What is the SolarWinds Sunburst Exploit?

Well it starts here. The hacker group called Dark Halo.![]()
They have been attacking political and corporate targets in America for a while.
They are also known as “APT29” or “Cozy Bears“.
https://en.wikipedia.org/wiki/Cozy_Bear
A mercenary group of “hackers for hire”, to the highest “nation state” bidder.
Dark Halo have recently attacked Multi Factor Authentication in Microsoft Exchange, Outlook Web access and finally SolarWinds Orion Products, with an exploit nicknamed “Sunburst“.
The Sunburst Exploit
The “Sunburst” exploit was a “supply chain attack”. A malicious backdoor was placed into SolarWinds.Orion.Core.BusinessLayer.dll which is a SolarWinds digitally signed component of the Orion software framework that communicates via HTTP to third party servers.
The attack’s execution is via an update package provided by SolarWinds’ legitimate website for the SolarWinds Orion platform, containing a trojan that opens up this backdoor, for attackers to enter into the organisation, when the update is installed.
Corporate espionage is common at the moment.
The hackers know that companies are struggling to function under the burden of Covid19, with few staff and everyone working from home.
Volexity provided research about this incident here:

The hackers also targeted FireEye a cyber security company.
FireEye refered to the hackers as UNC2452 and provided their own research here:
![]()
The SolarWinds Advisory & FAQ
As soon as the hack was announced SolarWinds released a security advisory:
https://www.solarwinds.com/securityadvisory
And a FAQ for those with questions:
If you think a SolarWinds Orion environment you manage may have been compromised, please make sure to follow the instructions contained within the above FAQ: “What should I do if I believe my environment has been compromised?”
Hotfix 2020.2.1 HF1 was previously released prior to the hack and mitigated against the hack if installed.
Following the advisory, SolarWinds released a hotfix 2020.2.1 HF2 which removed and further hardened against the vulnerability.
If the SolarWinds Orion Platform was running version 2020.2.1 the platform was not vulnerable.
Microsoft and SolarWinds worked together to remove access to the domains that the hackers used to exploit the SolarWinds DLL file.
Anti-Malware and Anti-Virus companies released updates to mitigate the infected files stopping SolarWinds from running the infected DLL.
Despite being inundated with calls and requests for help as many of their customers were worried about their own infrastructures (rightly so), SolarWinds had to work with government agencies to resolve the ramifications of the hack, so that national security was preserved. SolarWinds wanted to get the hotfix out as quickly as possible.
There were mistakes at SolarWinds it is clear and this is one of those times where in hindsight you can see that a malign influence was present, that managed to get code into some of SolarWinds releases. I’m sure more detail about how the software packages were compromised, will be revealed at a later date.
I work with four SolarWinds environments and have setup and maintained many others in the past. As the news unfolded, I was struck with horror at what was happening. I didn’t panic. I didn’t shutdown my servers. Many did.
I looked down the version list and realised with glee, that my installs were not affected. I was lucky. There were only three vulnerable platform versions.
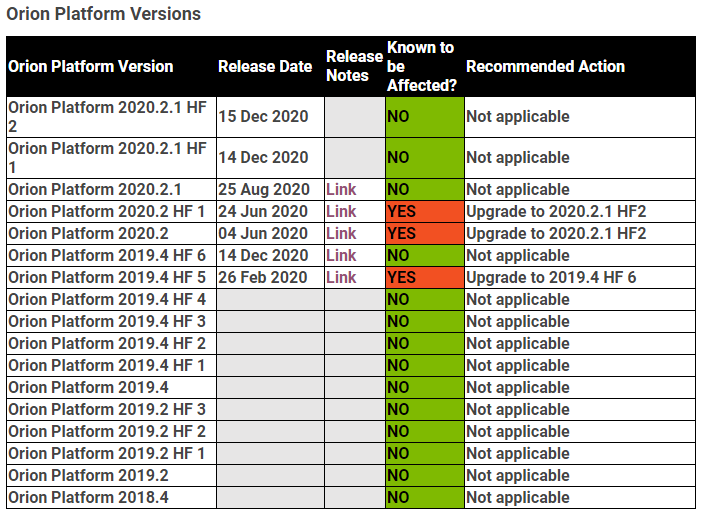
Then we made plans to upgrade anyway. Just to be on the safe side.
I am a monitoring engineer. All I want to do is get back to helping people improve their services, adding new equipment and applications into my platform so that I can provide pretty dashboards to my customers.
SolarWinds makes their customers lives a million times easier. SolarWinds is the best product on the market by far.
“Cozy Bears”, “APT29”, “Dark Halo”, made my life harder today.
The Misinformation
What made my life even harder was reading all the misinformation on Twitter, Reddit and other social media about the hacks and about SolarWinds products.
Now I love a good conspiracy theory, don’t get me wrong… But some of these theories were completely wrong at best and criminal at worst.
- I read that SolarWinds was responsible for a president losing the American election. The tweeter was blaming the file transfer software Serv-U for somehow influencing the Dominion voting tabulators during the election. The tweeter didn’t have a clue that this Serv-U software had not been hacked at all and was completely separate to the SolarWinds Orion product. (TECHNICALLY FALSE.)
- I found one tweeter naming SolarWinds staff as malign nation state actors who were obviously spies and were planting malware. This tweeter even claimed that the SolarWinds staff member may be deceased. (CRAZY.)
- I found tweeters blaming Obama, blaming Hilary Clinton for stealing information via the Dark Halo hackers. (THIS GETS OLD QUICKLY.)
- Other interesting theorists were blaming the CEO, stating that SolarWinds had been raided by the FBI and that the CEO was forced to surrender his passport just in case he left the country. (OF COURSE THE FBI WILL BE INVOLVED, IT’S A HACK!)
- Some claimed that the CEO had sold all of his shares as a means to devalue the company. (THIS HAPPENS.)
- The most amusing theory was the “solarwinds123” password access, to the update server. This was in fact a read only repo for updates for SolarWinds products. You would want it to be accessible for those wishing to download updates. (TECHNICALLY A FEATURE.)
The claims were wild and unsubstantiated and all of them could be explained by reasonable means.
It was disheartening and it was clear that most of the people commenting didn’t understand the software itself, or the functionality of SolarWinds Orion, or the way the exploit was carried out.
Some of the “misinformation bandits” are blatant political bots trying to provoke and some are uninformed individuals spreading crazy theories about the so called “cyber pandemic”. Check it out by clicking on the link. The creators of such videos always state that they will be banned tomorrow, or next week, or the next. Some day YouTube will ban them “apparently” but they never seem to disappear.
What Makes SolarWinds Special?
SolarWinds is a truly exceptional product that does things that no other product can do. It encompasses so many areas of infrastructure management. It is easy to see why a hacker would wish to target it and now with the release of HF2 and with the discovery of the methodologies utilised to exploit the platform it is clear that SolarWinds have got this covered.
Most companies with a practical response to incidents like these, will have experienced a couple of days monitoring black spot at most. With well trained monitoring engineers ready to respond to the update requirements and following the clear and concise instructions from SolarWinds, it is easy to see that when a risk appears, SolarWinds can handle it.
Most importantly SolarWinds have clearly learned from this already and the holes in their infrastructure will be tightly sealed.
SolarWinds didn’t have time to comment against these spurious claims on social media because they were busy making things better. Finding fixes. Fighting not only the pandemic but an unknown large, organised group of hackers, who have repeatedly attacked other organisations over the last few years.
We will all be worse off if we let these hackers destroy SolarWinds. It is not just a Software company, it’s a creative solution provider that allows myself and thousands of others to provide peace of mind, understanding and clarity to infrastructures all over the world.
Some of the most humble and knowledgeable people work for and with SolarWinds products. You can tell if you chat with them how enthusiastic they are and in demand the products are. Listening to and being a part of the SolarWinds MVP group, during this crisis has been inspirational. Everyone pulling together on Slack and THWACK to rebuild and move on, with as little fuss as possible.
If you knock them down, they come back stronger… fighting.
We keep on making things better and improving the day jobs of literally millions of IT staff.
These hackers make it harder for everyone but we won’t let them win.


Leave A Comment